It is the process of dealing with an incident to closure. Incidence response plans are written and designed to help organizations prepare for and manage cybersecurity incidents, minimizing business interruption and other losses.
An incident response plan is a document that sets out the procedures you will follow in the event of a cyber-attack on your business systems. This includes systems that might be compromised or attacked by malware or ransomware, but also systems with sensitive information – such as employee data.
An incidence response plan should include:
1
2
3
4
5
6
7
8
- Incidence response team schedule
- Role definitions and responsibilities
- Incident categories
- Priority levels and definitions
- Escalation Matrix
- Third party contact information
- Communication plan
- Lessons learned
Incidence response process
Incidence response is the process of detecting and analyzing incidents and limiting the incident’s effects (NIST 800-61 r2). In enterprise incidence response there is a larger scope with various threats, scenarios, systems, and devices. Enterprise computer incidents response teams (CIRTS) may handle variety of incidents including:
1
2
3
4
- Critical systems going down
- Lost/stolen laptops or cell phones
- Suspected insider threats
- Operational issues
The incidence response process is a six-step process as defined by NIST and illustrated in the figure below. It should be noted that the process is not linear but rather a cyclic process in which defenders through continuous learning and improvement better defend their organizations.
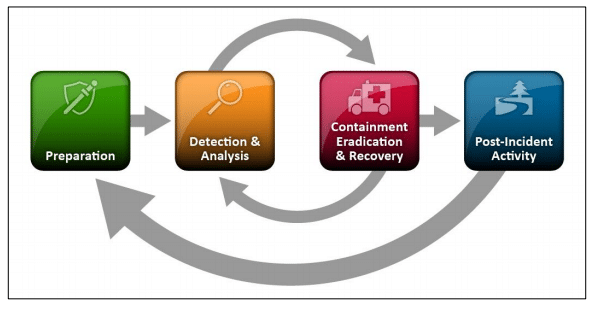
Preparation
To be better prepared, defenders need to have a clear understanding of their network identifying critical assets and data while having an asset register of all networks and devices within the organization. Incidence response steps should be detailed and security events to be investigated should be determined.
Detection & Analysis
Detection and analysis refers to the process of identifying a potentially hazardous situation and understanding the potential consequences. Detection is the process in which information about an event orthreat, is collected or detected for further evaluation. The detection process includes everything from indicators of compromise to identifying a specific artifacts or object associated with the detected information. Analysis involves the evaluation of just what is happening, where it’s happening, and its effect on the organization.
Containment, Eradication and Recovery
In the event of a cyberattack most often the goal is to contain, eradicate, and recover from the incident. Containment is limiting damage from the event so that it doesn’t spiral into something even worse. Eradication is stopping further damage from happening—especially lateral movement and data exfiltration. Recovery is restoring systems compromised to normalcy.
Post-Incident Activity
This is the most critical phase of all. It involves the lessons learned and documentation of phases not captured during the incident, as well as any that may be helpful in dealing with future incidents. A good incident documentation should be able to cover the who?, what?, where? and how? the incident occured. Organizations should conduct post-incident activity/lessons learned not later than 2 weeks of the incident response completion and include an executive summary as part of the report. A good example of the post-incident activity should include the following:
1
2
3
4
5
6
- When the incident was detected and by whom
- The incident scope
- The containment and eradication process
- Tasks perfomed in the recovery phase
- Areas where the CIRT team was effective
- Areas that need improvement from the team